ZASCO GPS Car Tracker – BRAND HISTORY – ZASCO GPS has been present on the market since 2014 and is specifically focused on providing vehicle security and protection service.

Over the years, the core product development has seen many challenges and major improvements while the brand has gained trust among the existing and potential customers. To demonstrate how the ZASCO GPS car tracker has evolved over time and what its benefits compared to other car security-related products on the market are, the ZASCO team decided to create a special sub page with an article revealing an in-depth story behind the brand.
The first part describes the existing car security solutions available when ZASCO GPS entered the connected car security market, outlining their main disadvantages and shortcomings that contributed to the development of a more advanced and reliable car security solution.
The second part addresses the most popular car theft practices and demonstrates how the ZASCO GPS car tracker helps its users react promptly in the event of any modern-day car theft cases.
The final section is dedicated specifically to the car tracker development and its improvements over the span of 5 years
GPS CAR TRACKER/TRACKING DEVICE
A GPS car tracker is a small navigation device equipped with a GPS receiver that enables determining the position of the object the tracking unit is installed into. The position of the monitored object is determined with the help of reference points – the satellites that send information to the ground. Each tracking device is in charge of sending signals to satellites which then transmit the location details to a server. This makes it possible to display a specific object on a map, which can be done by any authorized person.
GPS tracking systems generally include the following crucial components: a tracking unit, a server that receives tracking information from satellites, and a user interface that enables displaying the location of the monitored object.
The demand for car tracker solutions has increased in recent years, primarily due to a dramatic rise of vehicle thefts in urban areas. GPS car trackers are primarily being used for security reasons – to obtain a car’s location and enable vehicle tracking in case of a theft. GPS car tracking systems also serve as a great fleet monitoring solution that facilitates vehicle tracking for any large car or truck fleet company. Moreover, car trackers can also be of great relief for parents of teenagers, especially if a car tracking solution provides reports of teens’ actions behind the wheel.

Back in 2013, only passive vehicle GPS tracking systems were available, meaning that the monitoring was possible only for the time when the vehicle was moving. Our aim was to build an active car tracking system that would be capable of providing real-time information and vehicle monitoring even when a vehicle is stationary.
1. Loud real-time phone notification
At the time when ZASCO GPS car tracker was in development, most traditional anti-theft solutions, such as factory alarms or steering wheel locks, could not provide real-time location info. GPS tracker solutions that were able to do so were rare while the updates they provided at the time usually came with a long lag time, e.g. on a 5-minute basis or even later. The ZASCO GPS tracker, however, enabled real-time notifications with a possible delay of max. 1 minute and the refresh rate of 30 minutes if the vehicle is stationary. Besides, the system also records the whole trip history, which provides access to the history of all notifications detected for any vehicle

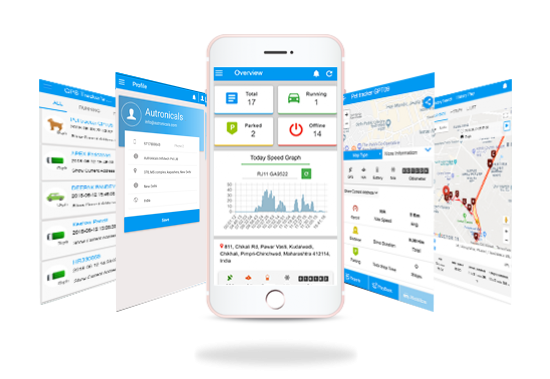
ZASCO GPS User interface via an easy-to-use Mobile app.
The ZASCO GPS once available on the market were mostly customized for fleet management, providing SMS notifications but not enabling any form of monitoring via mobile app. To check the vehicle location or manage the account, the user was required to log in via a personal computer. The ZASCO team thus aimed to develop a more comprehensive system that would enable vehicle monitoring and account management simply via the iOS or Android app on the phone.
TYPICAL THEFT PRACTICES AND HOW ZASCO CAR TRACKER DIFFERENTIATES FROM OTHER SIMILAR PRODUCTS
1. CAR THEFT WITH THE STOLEN CAR KEY
The simplest way to steal a car is to get its original key. This is usually one of a few non-invasive techniques, mostly suitable for older vehicles that still use regular old keys and are therefore unable to be hacked from the distance. This is often not an easy task since owners usually try to do their best not to leave their keys in visible places. However, if a criminal somehow gets access to the original key of the targeted vehicle, they can easily enter the vehicle and quickly drive it away. With the original car key having been stolen, the car anti-theft recognizes the criminal as the user, which, therefore, does not trigger the alarm.

2. CLONED KEY ATTACK
Another method that is also used for older vehicles is a cloned key attack. It usually happens near casinos or car repair shops, where car owners leave their vehicles for a longer period of time along with original car keys. This allows relatively easy access to owners’ car key fobs that can be stolen and cloned using a key fob duplicator. This machine actually enables copying the essential data to be used on another key fob. Once the key is cloned, the criminal returns the original keys to where they were stolen from and enters the car using the cloned car key fob to steal the vehicle. Since the cloned key fob contains the exact same data as the original one, the car is tricked into recognizing it as the original was therefore responds to the “door lock” message.
3. OBD PORT THEFT AND RF JAMMING
Over the recent years, a great number of expensive vehicles have been stolen all over the world with the help of key cloning, usually performed via the OBD II port. The OBD II port is basically a computer-based diagnostic system available in any car model manufactured after 1996. It is generally located under the car’s steering wheel and allows the repair technician to access the vehicle’s diagnostic information. This information is obtained via professional OBD readers any dealership and car repair shop usually uses. However, basic OBD readers can nowadays be purchased by anyone for less than $100. This somehow enables access to the most secure vehicle information practically to anyone.
Unfortunately, the OBD key cloning process has become a rather easy task and can be performed by professional thieves in just seconds. The hardest part of the process might be getting into the car without the alarm being activated. This might be done by smashing the side window using the end of the spark plug. Corners of side windows are actually considered “black spots” and breaking this part does not trigger the alarm.
As soon as the thief obtains access to the OBD port, the OBD reader can easily be connected to the OBDII port, which enables extracting a unique car key code within just seconds. This way, the programmed remote control can easily unlock the car and enable the thief to drive it away. The sad truth is the car key coding information is often not encrypted and thus easily accessible via the OBD II port.
RF Jamming
However, nowadays, many thieves use even more advanced methods, such as jamming technology, to get into the car without causing any physical damage on a vehicle and easily access the OBD port. Jamming attacks can actually be performed on any car that uses wireless key fobs and work by disrupting communication between the key fob and the receiver inside the car. The jamming process requires a device that operates on the same frequency as the car remote, which can easily disturb the door lock message. Moreover, many cars nowadays do not come with manual key locks, which, in the case of a jamming attack, totally disables the user to safely lock the car.
4. SMART KEY RELAY ATTACK
Smart key car theft, also called the “relay attack”, has become one of the most frequently used car-theft strategies in recent years, and has drastically contributed to the increasing rise in car theft cases, especially in areas with cars being parked close to houses during the night.
The process is relatively simple and involves two thieves working together. It does not require expensive professional tools, but only two radio-frequency-based gadgets – the relay amplifier and transmitter – that are available for purchase on the black market. One of the thieves first places the amplifier as close as possible to the house to detect the signal from the key fob. If the signal is successfully detected, it is then sent to the transmitter placed next to a vehicle. The transmitter actually works as a key fob and fools the car into recognizing alternative signals as the ones coming the original key fob. This can all be done in less than a minute and as soon as the car is unlocked, it can easily be started and driven away.
4. HOW OUR GPS CAR TRACKER EVOLVED OVER TIME
The initial version of the ZASCO GPS, launched in 2016, was designed in such a way that enabled it to easily connect with the OBD diagnostic port of any car manufactured after 1996. It came with an easy-to-use mobile app that enabled push notifications (“vibration detected” notification and other security notifications). The first app version included only the security features as well as the vehicle location info that enabled the user to monitor where the vehicle was 24/7. The first app update, which was released just a few months after the official product release, also enabled crash detection, SmartLock (beta) as well as the most requested feature – multi-vehicle monitoring. The latter enabled users to easily monitor and manage all the cars via one ZASCO GPS account. The feature allows users to add multiple cars to their accounts, easily switch between vehicles as well as receive notifications for each of the vehicles. Later on, the car tracker app was also upgraded with the paid back-up SMS as well as the call notification option. This is especially useful if the cellular data connection in a particular area is bad or if the ZASCO GPS user wants to avoid high roaming prices while traveling abroad.




Leave a Reply